ATCA 5000: From Russia With Love: JPMorgan, Cyber-Security and New Quantum Technologies
London, UK - 4th September 2014, 18:50 GMT
Hackers have stolen gigabytes of data from JPMorgan Chase, the biggest bank in the US and one of the largest banks in the world.
1. The sophistication of the cyber attacks appears to be beyond the capability of ordinary criminal hackers and could be nation state sponsored?
2. Are the sophisticated hackers trying to send a message that American and other global financial institutions can be disrupted?
3. Could the massive cyber attack have been backed by the Russian government in response to sanctions imposed by the US and EU over the crisis in Ukraine?
4. If hackers can steal such a large bank's data, if they can reach in that far, can they do anything else they want within the global financial markets?
5. If hackers collapse one major bank, can this not cause the entire financial structure to collapse like at the time of Lehman Brothers in September 2008?
 New Quantum Technologies & True Random Number Generation
New Quantum Technologies & True Random Number Generation
JPMorgan’s own investigators have found clues that a global network of computers available for hire by sophisticated criminals was used to re-route data stolen from the bank to a major Russian city. The hackers tapped computers from Latin America to Asia to send commands and obscure their identity while ferrying malicious traffic past one of the most heavily guarded networks on Wall Street. The use of a Russian-based data centre is one piece in a complex puzzle being constructed by investigators as they chase answers to urgent questions such as the attack’s motive, the hackers’ identity, and the possibility other banks may have been attacked or probed by the same group. JPMorgan’s chief executive, Jamie Dimon, has warned shareholders in annual letters that hackers’ efforts to breach the bank’s computers have been growing more frequent, sophisticated and dangerous. The bank expects to boost annual spending on cyber-security by 25 percent to about $250 million by the end of the year from 2013 levels, he wrote in April 2014. [Source: Bloomberg and other News Agencies]
Where's The Solution? New Quantum Technologies, Systems and Cryptography
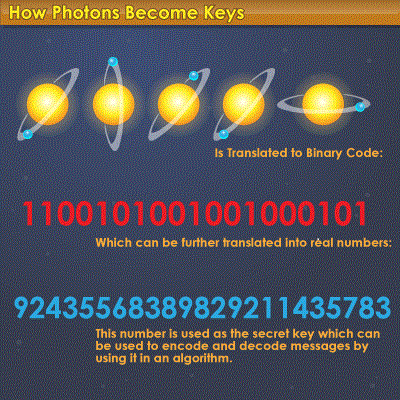
1. There are quantum-based technologies, which have been developed and rigorously tested for 20 years now, to create cryptographic keys "with lightning speed" by using the quantum properties of light particles, or photons, to generate random numbers to securely send data;
2. A hacker would be unable to predict the outcome of the quantum technology based random-number generator due to the randomness of the photons. The current random-number generators rely on mathematical formulas, which can be broken with high-speed and powerful computers;
3. New quantum technology systems represent the most robust solution for truly secure data encryption because they store or transmit information in ways that are unbreakable by conventional cryptographic methods;
4. If a snooper or hacker tries to eavesdrop on secure communications between two parties using quantum cryptography technology, then that communication can be scrubbed and the third party detected before information is stolen;
5. What the JPMorgan incident, amongst many others, demonstrates is that there is a growing demand for quantum cryptography products that can protect financial data from increasingly malicious and sophisticated cyber attacks;
6. The new quantum technologies could be used for safe and secure commerce, banking, communications and data transfer;
7. The new quantum technologies could also be miniaturised, ie, reduced to the size of a thumb drive or data-card reader at very low cost for consumers; and
8. The growing interest in new quantum technologies has led to the evolution of the "Quantum Innovation Labs" in London and the executive summary can be emailed on request by the mi2g Intelligence Unit.
[STOPS]
What are your thoughts, observations and views? We are keen to listen and to learn.
Best wishes

D K Matai
ATCA: The Asymmetric Threats
Contingency Alliance is a philanthropic expert initiative founded
in 2001 to resolve complex global challenges through collective
Socratic dialogue and joint executive action to build a wisdom
based global economy. Adhering to the doctrine of non-violence,
ATCA addresses asymmetric threats and social opportunities arising
from climate chaos and the environment; radical poverty and microfinance;
geo-politics and energy; organised crime & extremism; advanced
technologies -- bio, info, nano, robo & AI; demographic skews
and resource shortages; pandemics; financial systems and systemic
risk; as well as transhumanism and ethics. Present membership
of ATCA is by invitation only and has over 5,000 distinguished
members from over 120 countries: including 1,000 Parliamentarians;
1,500 Chairmen and CEOs of corporations; 1,000 Heads of NGOs;
750 Directors at Academic Centres of Excellence; 500 Inventors
and Original thinkers; as well as 250 Editors-in-Chief of major
media.
The Philanthropia, founded in 2005, brings together over
1,000 leading individual and private philanthropists, family offices,
foundations, private banks, non-governmental organisations and
specialist advisors to address complex global challenges such
as countering climate chaos, reducing radical poverty and developing
global leadership for the younger generation through the appliance
of science and technology, leveraging acumen and finance, as well
as encouraging collaboration with a strong commitment to ethics.
Philanthropia emphasises multi-faith spiritual values: introspection,
healthy living and ecology. Philanthropia Targets: Countering
climate chaos and carbon neutrality; Eliminating radical poverty
-- through micro-credit schemes, empowerment of women and more
responsible capitalism; Leadership for the Younger Generation;
and Corporate and social responsibility.

